Top Mobile Application Pen Test service in Canada
Manual techniques - Findings vulnerabilities that tools can't
In 2021, cyber attack will happen in every 11 Sec !
Get authentic VAPT results with our comprehensive Mobile Application Pen Test and skip the hassle of the traditional agency hunting process, proposal submission, consulting, to-and-fro negotiations, etc.

Our Research
Is your Mobile Application Security Capable enough to handle your customer's data's privacy?
Mobile Application Penetration Testing Key Concepts
- Authentication
- Authorization
- Confidentiality
- Availability
- Integrity
- Non-repudiation
- Resilience
Mobile has become your virtual ID card. Be it digital payment or finding a restaurant on a search engine or as important as your AADHAR details; mobile usage has become inevitable and so are the risks with mobile data. Trends like BYOD(Bring Your Own Device) have increased the exposure of sensitive company data. They all use mobile applications that are prone to attacks.
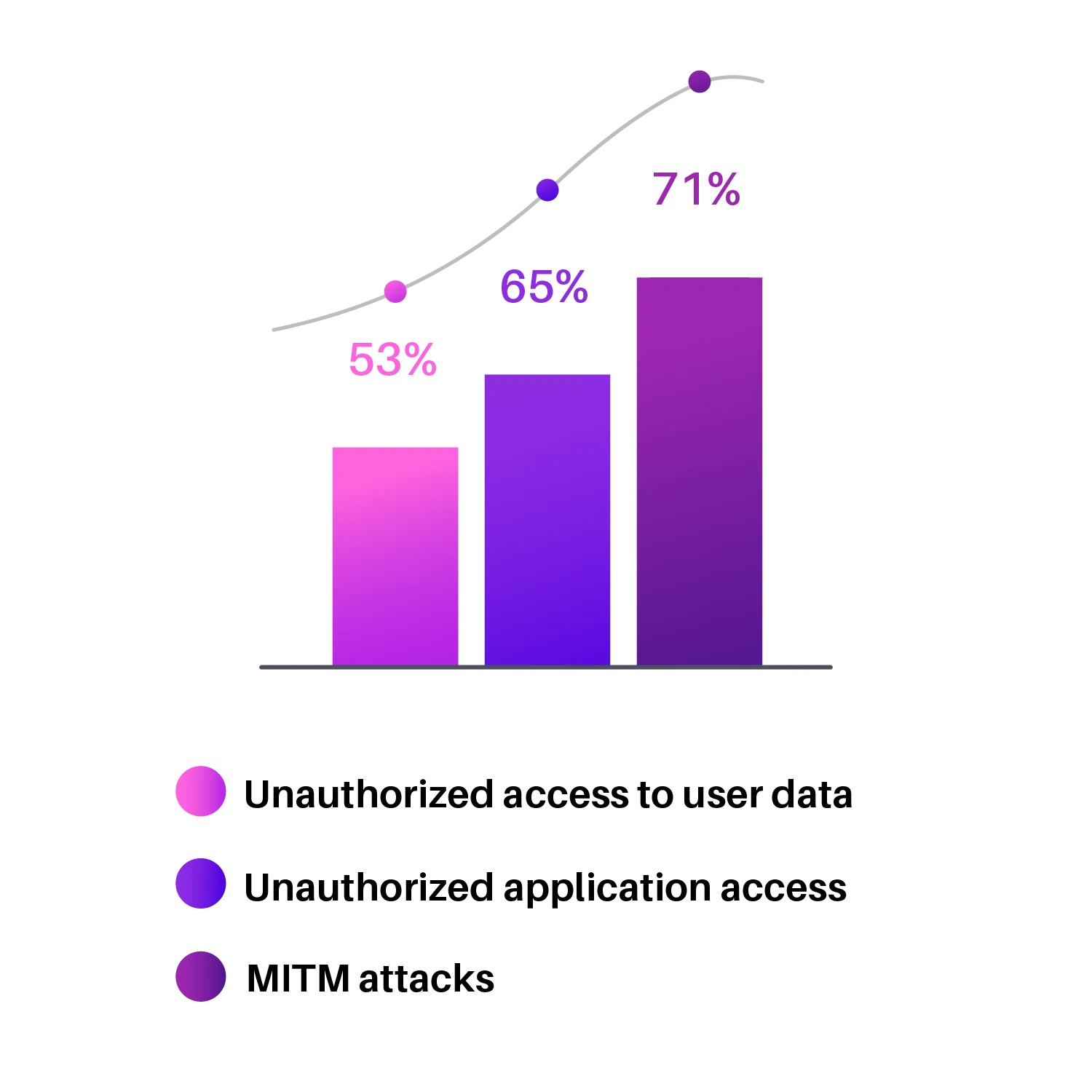
These are some common attacks that hackers use. It can be referred from the graph how much the data is exposed.
Phishing, Brute force, and SMiShing attacks are some common examples that are experienced by a common man.
We Believe In Transparent Pricing
Powering your business with world class Mobile App VAPT services.
Our Scope
Mobile Application Pen Test Scope
- Code Debugging
- Reverse engineering
- Console logging in production code
- Static Analysis
- Dynamic Analysis
- Business logic vuln.
- Server-side validation
- Admin/user account compromise
- Authentication brute forcing
- Root detection-method-bypass
- Local storage flows
- Sensitive data in logs, cache or shared storage
- Check if sensitive data stays after even log out
- Privacy and metadata leaks
- TLS check
- TLS weak encryption
- Bypassing SSL pinning
- TLS authentication flaws
- Insecure data storage
- Android server-side checks
- Client side injection (XSS)
- Username enumeration
- SQL injection
- Malicious file upload
- Check for all HTTP methods
- Session management
- CAPTCHA flaws & bypass
- IPC Security check
- Device DOS
- Permissions and digital signature data sharing issues
- Illegitimate applications
- Uncovered Components & Cross App Authorization
- Untrusted Code
- Sensitive information in application error message
- JS execution at WebViews
- Insecure permission setting through AndroidManifest.xml
- Buffer Overflow
IOS Application Security
- Exploring the iOS file system
- Insecure local data storage
- Broken Cryptography
- Binary Analysis
- Exploit Migration
- All used libraries
- MiTM on iOS
- HTTP traffic
- SSL/TLS traffic
- Bypassing certificate pinning
- Reverse Engineering
- Jailbreaking
- KeyChain dump
- Side channel leakage
- Screenshot caching mechanism
- Cookie Storage
- Device logging
- Keyboard cache storage
Top 10 Mobile Application Vulnerabilities by OWASP
- M1: Improper Platform Usage
- M2: Insecure Data Storage
- M3: Insecre Communication
- M4: Insecure Authentication
- M5: Insufficient Cryptography
- M6: Insecure Authorization
- M7: Client Code Quality
- M8: Code Tampering
- M9: Reverse Engineering
- M10: Extraneous Functionality
Expert cyber Security solutions, at Tailor-made costing
That fit every requirement
Our Process
Mobile Application Pen Test Process & Approach
Invesics's Pen-test approach goes beyond OWASP Top-10
Project Purpose
Requirement Gathering
Defining Scope
Automated VAPT
Manual PEN Testing
Review Analysis
Reporting Suggestions
Retest Certification
Experts strategy
Our Security Experts perform the following steps:
- Vulnerability assessment [VA] is based on the dynamic approach. The process of mobile application pentesting is recognizing potential entry points and vulnerabilities that can be exploited.
- Exploitation - Penetration testing [PT]is the use of tools and languages like PYTHON. Our security experts recreate methods of malicious hackers, trying to exploit the discovered vulnerabilities and attacking with various attacks like SQL injection, Buffer overflow attack, etc.
- In the discovery phase information is gathered which is generally called RECONNAISSANCE which gives a review of publicly accessible information and resources.
- It is basically done to intercept the traffic between the mobile application and API[Application Programming Interface]
- PURPOSE- To understand the working of mobile applications and trying to manipulate their functioning to check if any unwanted information is displaying.
- COVERED FACTORS: Data storage, Network communication between the application and server, Interaction with the platform, Security configurations, Source code
- Transfer knowledge
Experience in below Domains but not limited to:
Any Query?
Frequently Asked Questions
In case of Android app, you are requried to provide APK file. In case of iOS app, you are required to provide IPA file. If it is a manual based testing, along with previously mentioned things, we will need dummy credentials of each users roles that has access of respective apps.
In Mobile VAPT, pen-testing is done from the app UI - consist of BlackBox and GreyBox testing. In Secure code review, we will need access of your app code - which will be reviewed from Security perspective
Yes, Invesics is an ISO 27001 certified Company. Resources who will work on the assignments are CEH certified. Security Lead at Invesics is a double graduate having Masters degree in Cyber Security and Incident Response.
INVESICS is ISO 27001 certified company and hence we have all the compliance applies to handle your data privacy. Further, you will get digitally signed NDA before starting the assignment, this NDA is legally valid.
General test-cases for Mobile App pen-testing covers only some part of API calls - that are necessory to test core Mobile app functionalities.
API Pen-testing is having it's own multiple attack use-cases based on it's nature (i.e. REST or SOAP etc). Mobile pen-testing covers only necessory part of API calls limited to core app testing. Hence, it is recommended to have APIs Pen-test in scope to have maximum security.
You can convey that to you account manager, he will be there 24*7 to assist you. If your extra requirements does not fall under your selected plan, you will be given estimate for the extra work.
You can cancel the project anytime before signing NDA and you will get your money back. For more clarity, you can refer our refund policy here.
Relevant services
Supportive Cyber Security Services
Mobile Application Pen-Testing
Network Pen-Testing
Cloud Pen-Testing
Server Hardening
Under Attack? Need Immediate Assistance?
Reach out to our expert teammates to get solution for your Cyber Security concerns. We help to protect your organization from Data-breaches.